Comprehensive Cybersecurity Solutions
Sleep soundly with our state-of-the-art cybersecurity packages

Cloud security
Microsoft 365 Security and Security Hardening
Ensure your Microsoft 365 (M365) security configurations achieve the best policies. Maximise your defenses against cyber threats and data loss even for your remote workforce.
Endpoint Security
Protect your devices
Safeguard your devices and attain top-tier security standards, fortifying your defenses against cyber threats and data breaches, even for remote teams.


Identity protection
Protect your Identity
Ensure your identity protection settings meet the highest security standards, bolstering your defenses against identity theft and unauthorized access, even for remote teams.
Email Security
Protect your Inbox
Secure your email communications with top-tier protection standards.

Comprehensive Threat protection
A Multi-Layered Security Defence
- Cybersecurity assessments
- Security Awareness Training and simulated phishing training
- Managed Vulnerability Services (MVS)
- Zero Trust Network Access (ZTNA) and Privileged Access Management (PAM)
- Navigating your cybersecurity insurance renewals
- Security standards/controls compliance assessments
- Recurring and 0-day application patching
- 24/7 monitoring and remediation of breaches
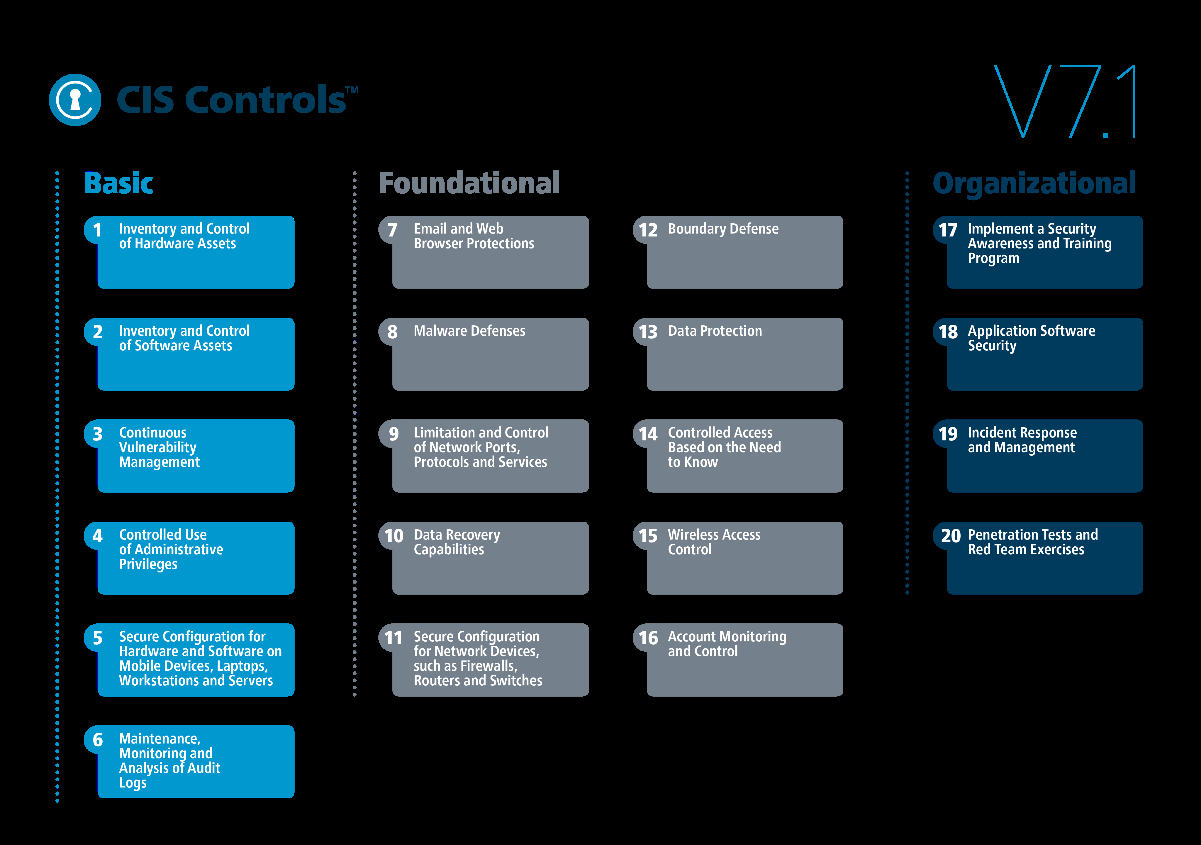
Cybersecurity frameworks
Complete online security, on all of your devices
We design and implement our solutions guided by the CIS (and later), NIST frameworks and the ASD top 35 mitigation strategies in mind. These frameworks are abstract enough to allow technology professionals to implement with their tooling of choice (Microsoft 365 in our case) and for business leaders to understand and engage in proactive discussion with those implementing the frameworks.
NIST Cyber Security Framework
Identify
Asset Management
Business Environment
Governance
Risk Assessment
Risk Management Strategy
Protect
Access Control
Awareness and Training
Data Security
Info Protection Processes
Maintenance
Protective Technology
Detect
Anomalies and Events
Security Continuous Monitoring
Detection Processes
Respond
Response Planning
Communications
Analysis
Mitigation
Improvements
Recover
Recovery Planning
Improvements
Communications